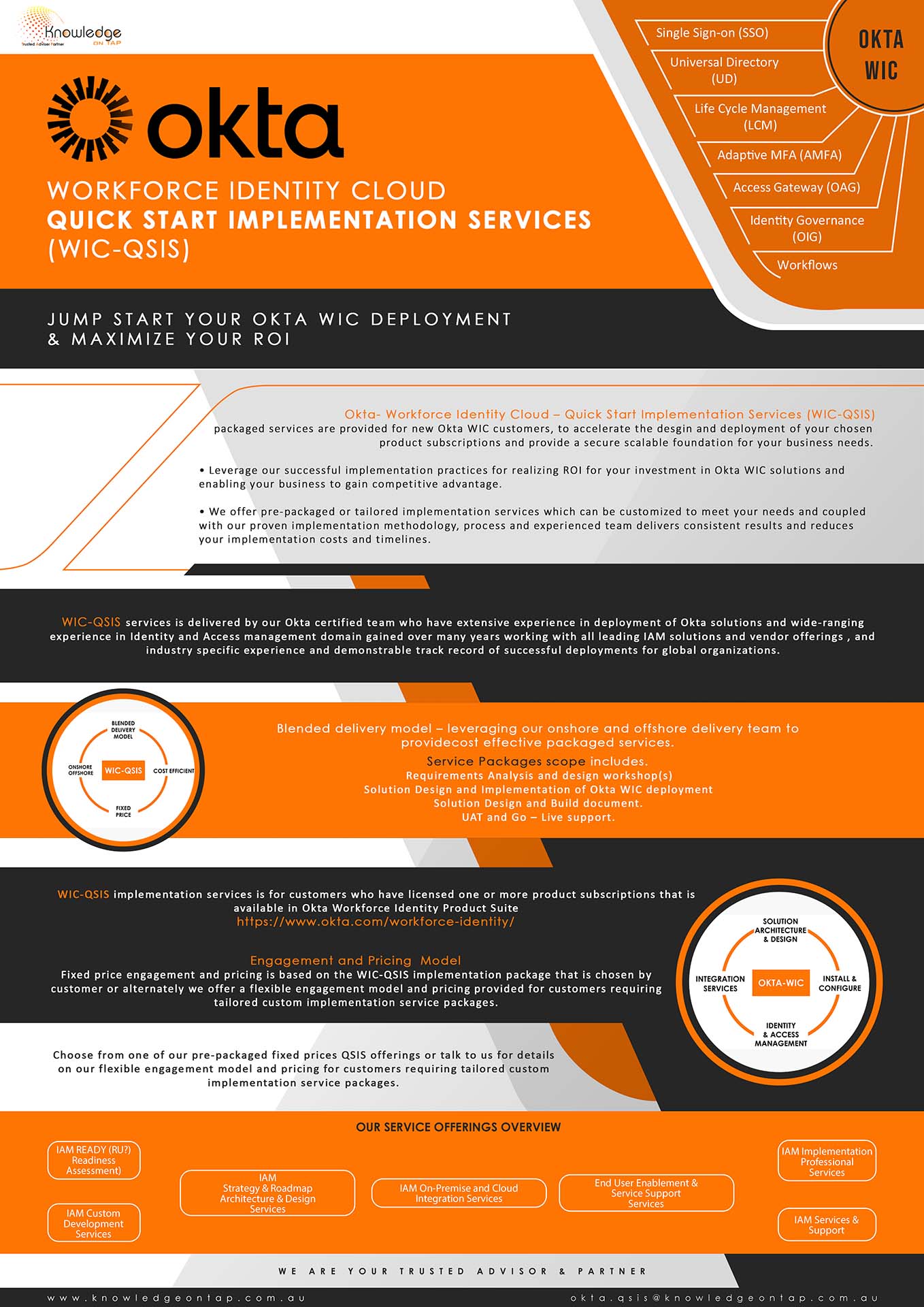
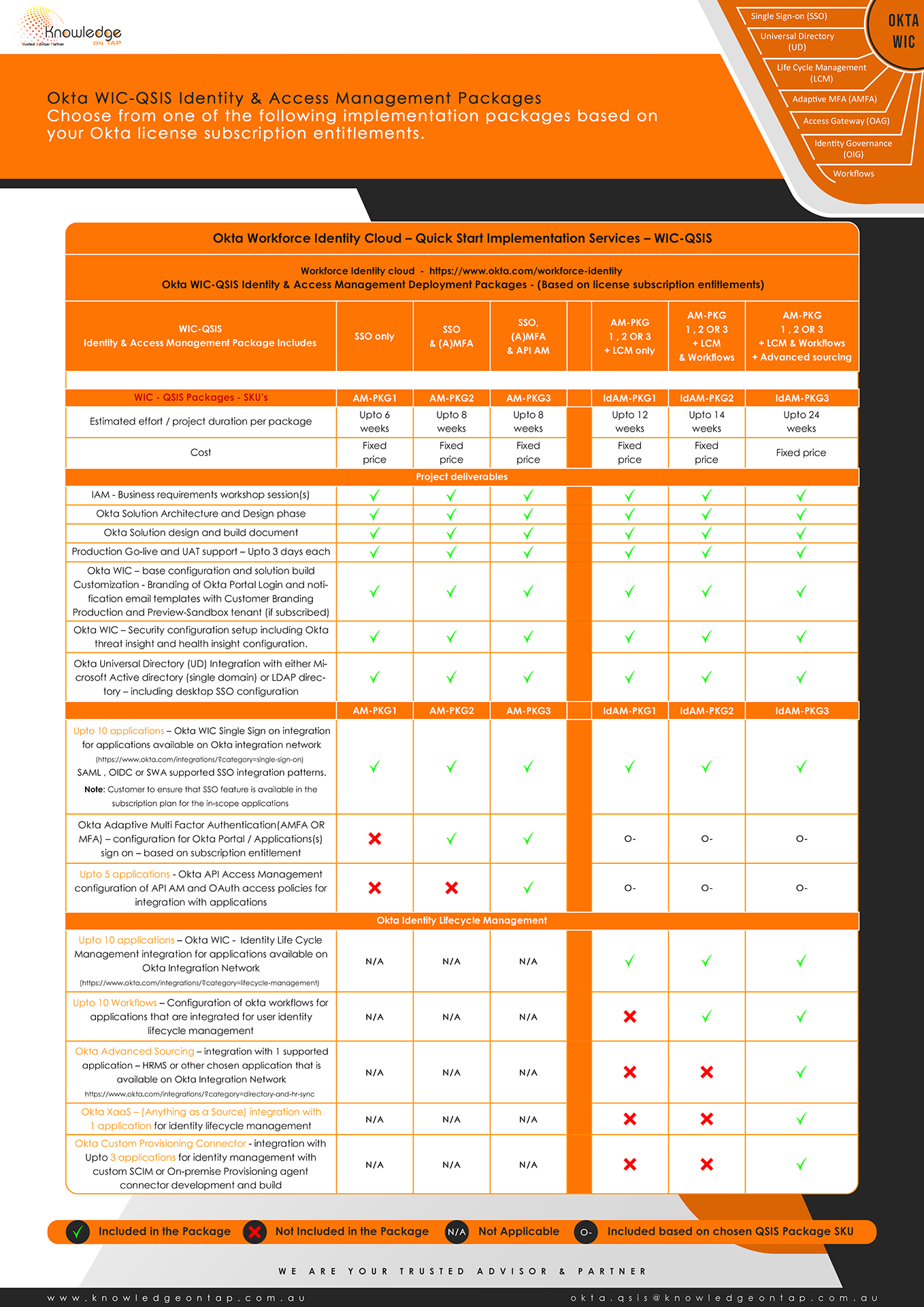
Digital Identity & Access Solutions
Traditional IAM solutions have evolved and a rapid pace and the leaders / visionaries in today’s world of Identity-as-a-service offering and traditional on premise IAM vendors are vying for market leadership and differentiation of service offering with a strong focus on providing a secure seamless online experience for businesses of all shapes and size including Government agencies who traditionally have not been leading the race to provide end to end online secure digital experience.
Solution Focus Areas
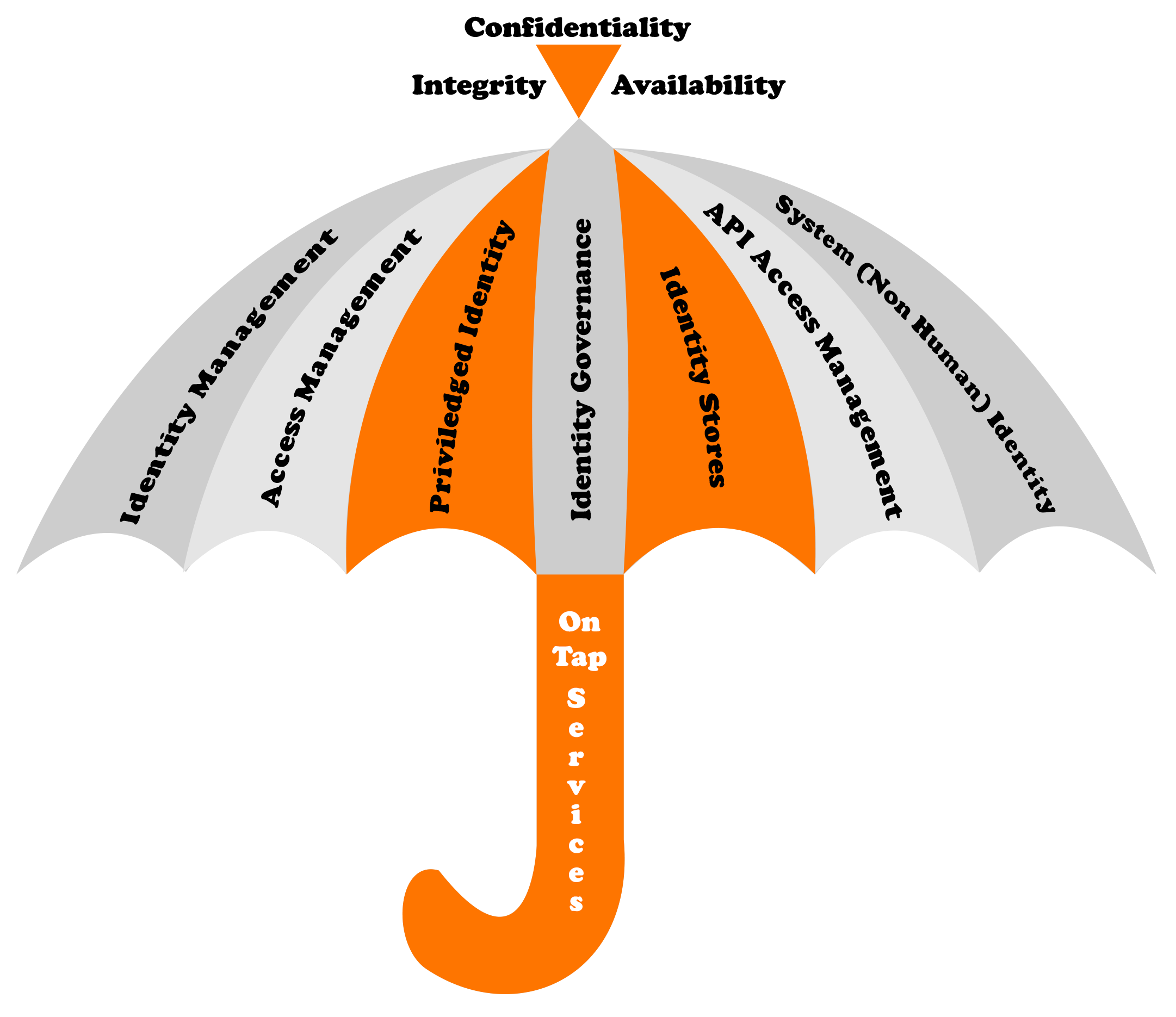
User Identity is the glue which enables business and Government to deliver – Secure and Seamless Anytime, Anywhere, Any Device Access to Any Cloud-based or On-premises Applications for Employees, Customers, Citizens, Partners, and other entities for Enterprises both Big and Small and Everything in Between”as our personal and professional lives intertwine in today’s rapidly changing world and is built on trust as we traverse our through our online avatars blurring the line between personal and professional personas.
There is an ever-growing need to address the requirements of customers and citizens alike and providing secure and seamless user access and experience across multiple delivery channels including Cloud, Mobile, and Social media whilst ensuring that the “Crown Jewels aka enterprise and Government data and Regulatory compliance and user trust is upheld and key to that is ensuring the triad of Confidentiality, Integrity and Availability of user information and data is protected at all times , whilst addressing the need to reduce budgetary and staffing constraints, Organizations are driven to continuously pursue ways to cost-effectively manage their security posture